The average work inbox is something of a minefield. According to Verizon’s yearly data breach report, phishing ranked as one of the top cybersecurity threats resulting in breaches in 2019. Then during the early months of the coronavirus pandemic in 2020, researchers identified a 350 percent increase in phishing websites. While email is a convenient tool that accelerates communication, organizations need an email security policy (like we have included in the Carbide platform) that reflects the modern nature of threats that leverage it.
In 2019, we saw several shifts in the way leaders in the information security sector approached security. Many of those shifts occurred in what we now view as best practices. Now with the sudden move to working from home, these and other security best practices for remote work are even more important. Read on to learn about the latest in email security policies, and how best to secure email in your organization during 2020.
Create an Email Security Policy That Works
Good security balances accessibility and workflow optimization with restrictive access that protects the company’s assets. In 2020, operational efficiency is critical for companies that want to remain responsive and relevant to shifting markets. However, security also remains a top concern as cybercriminals grow emboldened by previous successes. This year protect your company email with a security policy that works using these six tips.
1. Use a Trusted Email Service
Most companies already use an email service like Gmail or Outlook, so this first one is easy. It’s a good first step, but saying “we use Gmail” doesn’t count as an email security policy or procedures with a SOC 2 auditor.
It’s simple to set up a work email on the internet, especially if you start with a reputable service. Many popular email service providers, like Gmail and Microsoft, provide all the tools that a company needs to host a business email. Likewise, modern host exchanges represent another route that companies can take to create an organization email. Whichever route you choose, modern email services are essential to maintaining a safe email environment. They include things like:
- Regular updates: With developers constantly analyzing threats and patching potential entries, your email stays safer.
- Improved phishing filters: Email service providers have a robust repository of phishing and spam identification mechanisms, helping both stay out of your inbox altogether.
- Multi-factor authentication: It’s a best practice in security. Implement it in your email security policy.
2. Create Effective Spam Filters
Modern email service providers already filter out a certain amount of emails from ever reaching your inbox (or spam folder). However, that shouldn’t stop you from developing an effective set of spam filters on your own. Most providers allow you to adjust the spam filters on account to further restrict what makes it to your employees. Consider:
- Using whitelisting tactics on accounts that only should receive internal communications: Any contact that isn’t on the approved list will be blocked.
- Installing an email antivirus on computers used by individuals who send or receive external emails: Many antivirus software now integrate with your email to provide an additional layer of filtering.
Check your built-in spam tools and see if you need something to supplements them. These filters are critical for flagging suspicious emails before an employee gets tricked into clicking a malicious link.
3. Educate Your Users on Spotting Phishing Emails
Phishing is getting harder to spot. Although many people feel confident in recognizing a phishing email, 2019 saw a rise in highly personalized and targeted phishing attacks. Some of these fooled even the most astute recipients because they’re so well put together and personalized. Check out this email sent to a Carbide employee, claiming to be from our CEO asking them to complete a quick task. This would lead to social engineering by text or phone to get even more information or access.
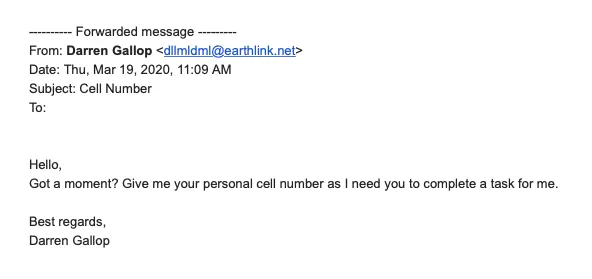
A security awareness training program that focuses on spotting phishing emails can reduce the likelihood that an attempt will be successful. Make sure to talk about some of the latest innovations in phishing, such as the business email compromise attack.
Make these trainings routine. They’re not effective if they only happen annually. Aim for a refresher on email security every few months.
You can also help users avoid phishing emails by establishing clear policies on email communication. Layout guidelines on:
- When, why, and from which executives or managers users can expect to receive emails: Make it clear that random emails asking a user to carry out a task are not the norm. A manager’s email from out of the blue instructing you to “install this new antivirus software” should immediately raise red flags.
- What to do if they suspect a fraudulent email: Train users to reach out to colleagues in other ways and forward the email to IT. You should have a designated person or team email address where people can send anything suspicious.
4. Get Smart About Attachments and Links
Attachments and links are the biggest ways that malware infects a system. Make sure your email security policy addresses them.
Attachments can prove easy to overlook. In 2019, Trend Micro found that the most common file types containing malware were those that an office worker might expect to receive. These included PDFs, Excel spreadsheets, Word documents, and zipped folders. Additionally, many of these arrive disguised as invoices, database exports, or some other seemingly legitimate business document. Hackers can easily embed code into an attachment that activates once the file has been downloaded.
Links are also dangerous. They’re easy to spoof (or make it look like it goes somewhere other than where it does) and may send a user to a legitimate-looking login page that collects credentials.
Establish a policy against downloading attachments or clicking on links from unknown senders. Support this policy with:
- A list of safe URLs where users should log in to any business resources in a secure browser.
- A method to securely send files that doesn’t rely on email. You also want to be clear about what information can be shared using a password management tool and what is okay to send using a file-sharing tool like Google Drive.
- A secure method for acquiring invoices or other legitimate business files from vendors or suppliers. For example, train users to log in to accounts and download order histories directly.
5. Treat Unsolicited Correspondences with Care
For email accounts that only receive internal communications, it’s helpful to adopt a whitelisting strategy, where only approved contacts make it into the inbox. For accounts that receive emails from external sources, that’s not practical. Therefore, train users to treat unsolicited correspondences with care, especially if they seem to be offering something. Some policies to adopt might be:
- Do not respond to unsolicited emails offering something or making demands.
- Verify the identity of the sender, either by cross-referencing them on LinkedIn or looking into the company they claim to represent.
6. Protect Email Addresses
To arrive in an inbox, a hacker first needs the email address. Therefore, train users to treat email addresses as “need to know” information. In other words:
- Prohibit posting work email addresses on website pages, social media, or other public forums.
- Use a catchall email for support, customer service, or other public-facing inquiries.
- Only give out emails to qualified leads, vendors, suppliers, and business partners who need it.
Be Smart About Security – We Can Help
There are no shortcuts when it comes to email security. A policy that involves best practices can help keep a company safe, preventing malware or phishing attacks from damaging the business. Turn your inbox into an efficient, effective communication tool that it is by keeping spammers and hackers out.
If you’re looking for new security tools to protect data at your company? Check out what we have inside the Carbide platform.


