It can be overwhelming for small businesses and startups to meet the security and privacy requirements for doing business with the U.S. federal government. In this article, we’ll discuss FedRAMP compliance including the following:
- What FedRAMP compliance is
- Why FedRAMP was created
- Who governs FedRAMP authorization
- Why organizations need to comply with it
- How organizations become FedRAMP authorized
- The potential impact levels of FedRAMP
- 6 tips for small business and startups
- The difference between NIST and FedRAMP
Brief Overview: What is FedRAMP Compliance?
The Federal Risk and Authorization Management Program (FedRAMP) is a government security program that brings a standardized approach to streamline the process for assessing and authorizing Cloud Services providers (CSPs) and cloud services. The program is specifically for companies looking to work with federal agencies and store, process, or handle federal information.
FedRAMP provides guidance for meeting a common set of security standards to ensure cloud technologies are securely adopted by organizations working with the federal government. It is based on NIST standards and uses a risk-based approach to security.
Generally speaking, achieving compliance with FedRAMP includes implementing security controls, passing security assessments, and maintaining ongoing monitoring of their environments.
Why was FedRAMP created?
The creation of FedRAMP was in response to the federal government moving from legacy systems and adopting cloud technology. To prevent federal agencies from being compromised as they migrated federal information to cloud services, there had to be a consistent, standardized, and government-wide approach to managing security and privacy.
Who governs FedRAMP authorization?
The Joint Authorization Board (JAB) governs the FedRAMP program and is comprised of the Department of Defense (DoD), the General Services Administration, and the Department of Homeland Security (DHS).
The JAB sets the baseline security standards that Cloud Service Providers (CSPs) must meet to become FedRAMP authorized and to work with federal government agencies.
FedRAMP authorization is performed by third-party assessment organizations (3PAOs) that are accredited by the FedRAMP Program Management Office (PMO). These organizations are responsible for conducting security assessments and issuing authorizations for cloud products and services.
Why do organizations need to comply with FedRAMP?
FedRAMP authorization is required for any company that wants to provide cloud products and services to the U.S. federal government. Compliance with FedRAMP demonstrates that the business has met the security requirements set forth by the federal government and that its information systems and data are secure.
Third parties that process, store, or transmit federal information on behalf of a federal agency are required to be FedRAMP authorized. The process of achieving FedRAMP compliance can take longer and be more tedious than expected, so starting early is a good idea.
Ready to work towards FedRAMP compliance but not sure where to start? Talk to our team to learn how Carbide can support your journey.
How do organizations become FedRAMP authorized?
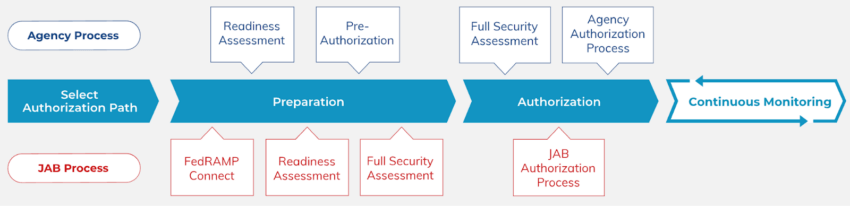
There are two ways to authorize a CSP through FedRAMP – Joint Authorization Board Authorization and Agency Authorization.
While the Agency Authorization process pairs a CSP with a US Federal agency that follows them throughout the entire FedRAMP authorization process, the Joint Authorization Board process leverages external organizations that evaluate and review if the CSP meets FedRAMP requirements.
These approaches can be broken down into three phases – Preparation, Authorization, and Continuous Monitoring. The ultimate goal of each phase is to acquire a new FedRAMP Marketplace designation. The designations – FedRAMP Ready, FedRAMP In Process, and FedRAMP Authorized are earned as CSPs move through the three phases.
Source: https://www.fedramp.gov/
Joint Authorization Board Authorization
The Joint Authorization Board approach is a provisional authorization process and requires an external group called the Third Party Assessment Organization (3PAO) to evaluate the CSP’s security controls and procedures. This evaluation process also includes the CSP and their 3PAO putting together a Security Authorization Package consisting of a System Security Plan (SSP), a Security Assessment Plan (SAP), a Security Assessment Report (SAR), and a Plan of Action and Milestones (POA&M). If no remediation is required and FedRAMP requirements are met, the JAB will issue a Provisional Authority to Operate (P-ATO). The P-ATO gives the cloud service provider the authority to begin periodically working with federal agencies.
After receiving their P-ATO, CSPs must undergo continuous monitoring to ensure their security controls are being maintained and comply with FedRAMP requirements. The 3PAO conducts this continuous monitoring to identify potential vulnerabilities in the company’s systems based on the periodic reports the CSP submit to them.
If the provider’s security controls are appropriately implemented and continue to comply with FedRAMP’s requirements, the JAB will issue a formal Authority to Operate (ATO), giving the CSP the authority to begin working with federal agencies permanently.
Agency Authorization
Becoming FedRAMP authorized via the Agency Authorization route is also a rigorous security assessment process. When working with a US federal agency, acquiring a FedRAMP Ready designation through Readiness Assessment Report (RAR) is optional, but the FedRAMP Program Management Office highly recommends it.
Next, the agency will review the Security Authorization Package that the CSP and their 3PAO developed. The Security Authorization package consists of four components:
- System Security Plan (SSP)
- Security Assessment Plan (SAP)
- Security Assessment Report (SAR)
- Plan of Action and Milestones (POA&M)
If no remediation is required, the agency will submit for the CSP to receive their Authority to Operate (ATO). Similar to the JAB process, after gaining their ATO, CSPs must provide monthly continuous monitoring documentation for review before receiving permanent authorization.
What are the potential impact levels under FedRAMP?
The FIPS Publication 199 divides FedRAMP’s impact levels into three categories: low, moderate, and high based on The Federal Information Security Management Act (FISMA). FISMA is the infosec framework all companies and organizations must comply with to work with the Federal Government. It applies to all third-party providers, where as FedRAMP only applies to cloud service providers.
The impact levels defined by the FIPS Publication give organizations an idea of the potential impact a security breach of FISMA’s security objectives (confidentiality, integrity, and availability) could have on their systems and people.
FIPS Publication 199 defines these potential impacts as:
Low Potential Impact
The loss of confidentiality, integrity, or availability could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals.
Moderate Potential Impact
The loss of confidentiality, integrity, or availability could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals.
High Potential Impact
The loss of confidentiality, integrity, or availability could be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or individuals.
6 Tips to Get Started on FedRAMP Compliance
Small businesses can kick-start their FedRAMP compliance process by following FedRAMP’s tips for small businesses and startups:
- Perform a gap analysis and learn how your current security posture measures up.
- Have cross-department buy-in. The process will require leadership to get technical teams to work with auditors to complete security assessments ASAP.
- Get a federal agency partner – you need to receive an Authorization to Operate” (ATO) to work with a federal agency, so preferably get a partner that is using your product or services or plans to.
- Define the scope of your offering – and be ready to accurately describe how your system securely stores, processes, or handles federal information.
- Remember, security isn’t a one-time event; it requires continuous monitoring and maintenance.
- If you have more than one product, don’t take on too much at once and risk not being able to meet security requirements.
What is the difference between the NIST framework and FedRAMP?
NIST, or National Institute of Standards and Technology, is a non-regulatory agency of the U.S. Department of Commerce. As a framework, NIST develops and publishes standards, guidelines, and best practices for information security and privacy in general. FedRAMP, on the other hand, is a government-specific program. Its controls and requirements are based on the NIST 800-53 standard, which provides guidelines for security controls for federal information systems.


